If you use a computer, and pretty much everyone does, you’d better brace yourself for some jaw-dropping statistics. Every 39 seconds, a computer is hacked. That’s almost 2 computers per minute being hacked, with an average of 70 records being stolen. How are hackers pulling this off? Well, 80% of all hacks are tied to a compromised password.
Russian hackers are the fastest – they can hack into a computer in about 18 minutes, regardless of the strength of the password. And regardless of who is doing the hacking, cybercrime is profitable – it’s become the most profitable criminal activity in the world – surpassing the worldwide illegal drug trade! Cybercriminals work fast – they’re able to steal 75 records every second. And once a business suffers a data breach, it’s a tough road to recovery. In fact, 66% of businesses claim they probably couldn’t recover from a significant data breach.
How to Stop the Hacking
Of all the statistics you just read, here’s one you really need to remember: 99.9% of all hacking can be prevented by one thing: 2-factor authentication, also called 2-step verification. You’ve probably heard about 2-factor authentication or have seen it offered on various apps and websites. Most people simply ignore it, while others insist on having it for added protection.
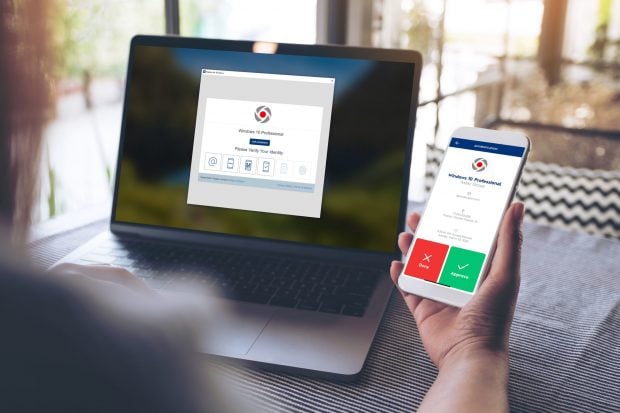
So, what is 2-factor authentication (2FA)? Most people think a username and password will provide adequate protection from hackers, but sadly, it won’t. As its name implies, 2-factor authentication adds a second level of protection, because in addition to a password it requires a log-in authentication code that’s sent to you via email or text to your cellphone or other device. Without the code, also called a “one-time password” (OTP) you can’t access the account. It can also use your fingerprint, or voice or face-recognition technology. Some services send a link, which bypasses the need to enter a code.
Let’s say you’ve enabled 2-factor authentication on one of your online accounts. You enter your log-in information, including your password. Before you’re granted access to your account, you’re sent a text with your 2-factor code, which you must enter to gain online access. Without it, you’re locked out. That means if a cyberthief in hacked your password, he or she couldn’t gain access to any of your accounts because they would have to be next to your cell phone to view the code you were sent. It’s peace of mind for the user.
Are there Problems with 2-FA?
Before you sit back and relax thinking that 2-step verification has you covered, there are some problems with this technology that you should be aware of. First of all, if a code is sent to your cell phone and your cell phone is lost, stolen or otherwise incapacitated, you won’t be able to receive it and you’ll be locked out. Until your cellphone is located or working again, or you begin using a new cell phone with the same number, nothing you do will be able to get you into your account.
Receiving your 2-factor authentication code on your cell phone is one thing, but using emails for your verification is not as secure. Let’s say the cybercrook is out to steal your 2-FA; if you use a cell phone, they’ll need to be standing next to you to steal the code that’s sent. But if you opted to receive verification via email, a hacker could easily get into your email account and steal the code. If you use the same email address for multiple account verifications, the cybercrook will have access to all of those.
Here’s something else to consider: while the 2-factor authentication will provide a good way to keep others out of your accounts, if a hacker is blocked, they may have the capability to twist things around and lock you out of your own account. They simply reconfigure the 2-FA and block you.
Use an App
Apps are now available to generate a very strong code for your devices. You’ll find them on the app stores and they’re now offered by major retailers and many of the major social networks. One of the more popular apps is Google Authenticator. If you have a Google account, just download the app and follow the easy-to-use steps. Microsoft also has its own version, the Microsoft Authenticator.
On the social media side, Facebook has its own authenticator. Once you turn on 2-FA, it’ll provide codes directly from Facebook, but it is only good for Facebook authentication – not for other sites. It’s the same with Amazon – they have their own 2-FA generator that’s used only for Amazon. The good news is that more apps are on the way.
Other Steps to Take
While 2-FA helps prevent hackers from logging into your accounts, you’re still at risk because your personal information is available to hackers on people-search sites. In fact, one stat shows that the average person can be found on 46 different people-search sites. You need to reduce your risk of exposure by removing your personal information from all of those sites.
Doing this certainly won’t take away every potential hacking opportunity, but it will help keep your private information private. Never lend your cell phone to people you don’t know and trust implicitly, to keep your 2-FA codes out of the wrong hands. And following safe Internet practices is another step to keep you safe from hackers and cybercrooks.



